PREMIUM ULTIMATE
Below is the process described for connecting qibb with Okta Workforce Identity Cloud using OpenID Connect.
| Step | Description |
|---|
| 1 | Request the qibb IdP URL | To get started, you will need the qibb IdP URL, which will be used by redirects between qibb’s Sign in Page and your Identity Provider. You can reach out to our Support Team to retrieve the qibb IdP URL.
|
|---|
| 2 | Setup an app integration in Okta Workforce Identity Cloud | You will need to register an application in in Okta Workforce Identity Cloud admin console with type “Web Application” and using the qibb IdP URL. Follow the official guide of Okta. Log in to the Okta Admin Console. Navigate to “Applications” and click “Create App Integration.” Configure the application to use OpenID Connect (OIDC) as the authentication protocol for the Web Application type Configure the OIDC settings, including Redirect URI (qibb IdP URL).
You can restrict access to qibb for a specific set of users or group under the section Assignments. After creating the application under Client Credentials section copy Client ID & Client secret. Copy the Okta Tenant ID from the top right side under your user account information.
|
|---|
| 3 | Provide the App Information to Support Team | |
|---|
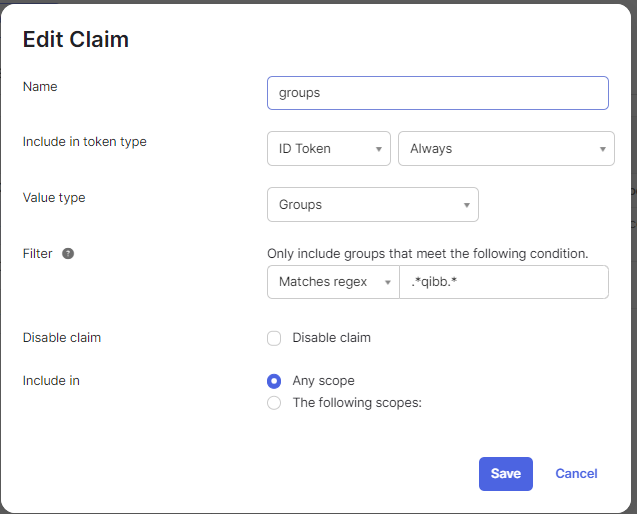
| 4 | Defining group mapping in alignment with Support Team | Group mapping enables you to determine the specific Qibb permissions that a group of users should receive automatically (such as an assignment to a qibb group), depending on their membership in an Okta group. You will need to add groups attributes into the claims.
Provide a list of Okta group names, that need to be mapped to a specific group in qibb, to our Support Team. There are default groups and patterns available for reference. Once the group mapping is set up using the group name, members of that specific group will be automatically assigned to the corresponding qibb group after each login. If you wish to change or extend the group mapping in future, contact our Support Team with the request to update the configuration.
|
|---|